NordVPN accused of blackmail, sued TorGuard
Ah, just the other day I was talking to a colleague about how to “calm down”, lately everything is in the VPN industry. I guess I spoke too early, because things have turned wild!
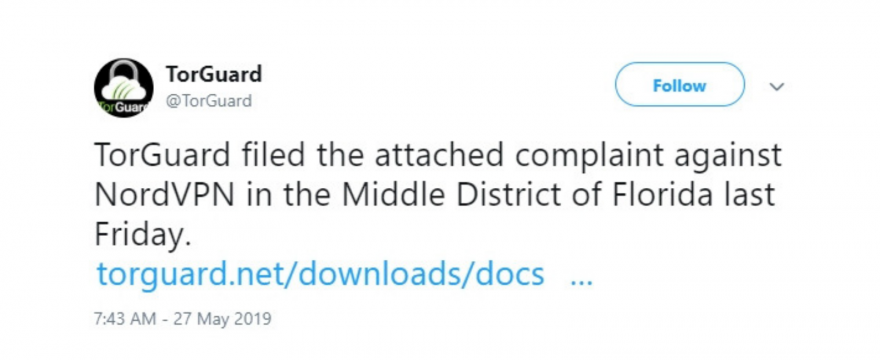
Unexpectedly, TorGuard recently announced on Twitter that it is trying to sue NordVPN and Canadian web design and development provider C-Seven Media, Inc.
You can read the full copy of the lawsuit filed in the Florida District Court in which TorGuard opposes NordVPN and C-Seven Media on three counts:
“CADRA”)
- LAW ON BREACH OF SECRET SECRETS OF FLORIDA UNIFORM (“FUTSA”)
- TORTIOUS INTERFERENCE WITH TORGUARD’S BUSINESS RELATIONS
So, why US TorGuard sues Panamanian company NordVPN in Florida, recently linked to misleading advertisements and “dishonorable” registration of 735,000 IPs from ARIN via Micfo?
This video by Tom Spark should summarize the whole fiasco, but if you still need a quick background, I have compiled a short list of events as highlighted in the lawsuit:
- “ an unidentified individual appeared uninvited at a staff member’s personal residence requesting a conversation about the VPN industry. ”
- A TorGuard employee also received emails to the personal account of an“ unknown individual ”from competing VPN services.
- The individual later revealed that he was from NordVPN using a legal [@] nordvpn.com email ID that was found to have “TorGuard’s confidential and trade secrets”.
- A service provider based in the United States, he claimed that Nord had links to or controlled C-Seven Media (previously, TorGuard had been granted access to “private information”).
- TorGuard is allegedly blackmailing NordVPN to remove negative YouTube posts from affiliate company Tor (Tom Spark Reviews), otherwise classified information will be leaked.
- Following the conclusion of C-7 and TorGuard’s relationship, NordVPN and C- Seven Media carried out DDoS attacks, and one was carried out on November 23, 2018, aka Black Friday.
- TorGuard seeks judicial and final assistance, compensation “in excess of $ 75,000,” recovery of all lost profits “in light of these DDoS attacks.
NordVPN’s Official Response to the Lawsuit
After reading the lawsuit, I immediately contacted NordVPN to comment on the allegations, and they referred me to a blog post about the case ..
NordVPN claims it all started after they found a TorGuard server configuration file and decided to analyze it, which led to the discovery of pirated keys, a bunch of infrastructure IP addresses, including the IPS of their servers for identity verification and similar assets.
Further analysis revealed that the server is not protected and contains sensitive information that could cause great harm to TorGuard and its customers in the wrong hands. This is where NordVPN decided to reach out to TorGuard’CTO, Keith Murray.
He immediately involved TorGuard’CEO, Benjamin Van Pelt, in the conversation and NordVPN provided the IP of the affected server, asking for nothing in return, so TorGuard could fix their vulnerability.
We still have trouble wrapping up what happened next. On Monday, May 27, we received information about a lawsuit filed against us by the law firm Losey PLLC. TorGuard has also accused us (probably by mistake) of an unrelated Canadian web design company conspiring against them, hacking their servers, carrying out a DDoS attack on Black Friday and physically intimidating someone – and this is a very abbreviated version.
We intended to do the right thing in the right way and compete fairly without damaging the industry, which is why we were so shocked by the response. We will immediately move to the dismissal of TorGuard’s lawsuit, but as long as we are on the topic: filing false and malicious lawsuits and publishing untrue and misleading information is against the law. So we are suing for defamation and defamation.
Is TorGuard just throwing Aspersions at NordVPN?
True, it’s hard to know who’s right, not. The VPN industry is becoming increasingly popular, especially at a time when governments are demanding more control, imposing laws requiring data retention and mass surveillance.
As such, strong competition between service providers is expected and this is not the first a way to witness how different VPN providers openly attack each other both in court and online. Remember that scandal in which ProtonVPN and PIA were involved?
NordVPN is also mentioned in this case because of its connection with CloudVPN (based in the USA), which has ties to the Lithuanian company Tesonet. It was later revealed that CloudVPN is just a payment processor for Nord, as the Panamanian headquarters makes transactions difficult.
The Panamanian vendor regularly visits the VPN industry news section due to various allegations against their service (a lawsuit involving Hola VPN) , when in reality you can rarely ever find any consumer who has a bad experience about the product and its capabilities.
TorGuard is among those in action, with an associate member of “Tom Spark Reviews”. he often criticizes Nord, as long as he himself has a strange background. That Spark guy is said to be the same Kevin Wadala and a person known as Corelio Guardez, who promotes TorGuard but degrades Nord!
I feel it too ’It is important to note here that this is not the first time TorGuard has been accused of security breaches. In 2015, a competitor accused VPN.ac of copying browser designs and APIs implemented in their browser and proxy service.
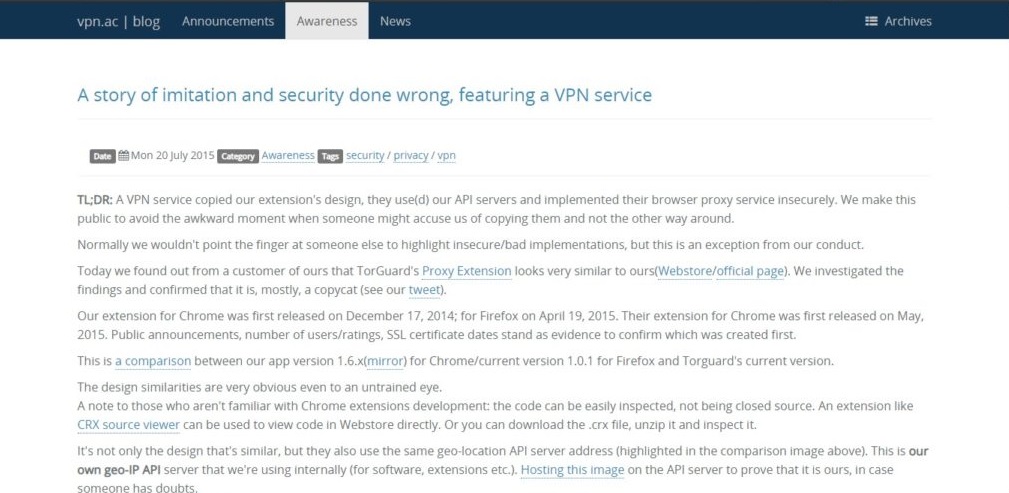
See the vulnerabilities on found VPN.AC on his blog:
Torguard stores credentials in clear text; We pass XORing passes to protect it from spyware that will search clear text credentials everywhere;
To play: add some credentials and save them> right click on extension> Browse Popup> Resources> Local Storage
Torguard gets an updated list of proxy gateways over HTTP (again in clear text ); we get them via HTTPS (A + to Qualys / Mirror Results): from Torguard’s background.js, from our background.js;
The obvious risk of providing a server IP address via HTTP is that they can be easily hijacked in MitM attack;
Torguard’s HTTPS proxy is very insecure: it uses insecure codes like RC4, supports SSL 3, is vulnerable to a POODLE attack, doesn’t it provide an indirect secret. He gets an infamous Class C on the Qualys test. Result Mirror 1, Mirror 2 (to display the original result). And that’s our result / mirror (FS enabled, no weak codes, only TLS 1.1 and 1.2 support);
Wrapping Things
Stop this mud throwing and toxic attacks! You should join hands trying to raise awareness about mass surveillance and data retention which are BIG PROBLEMS.